



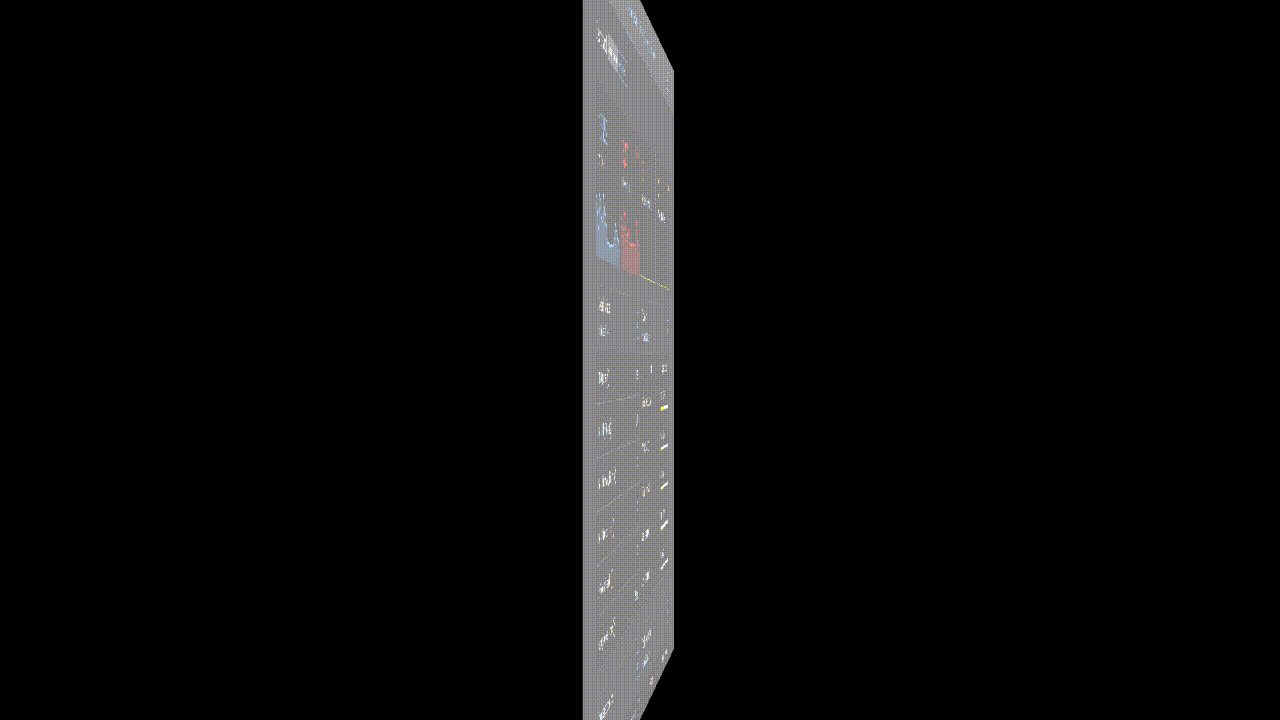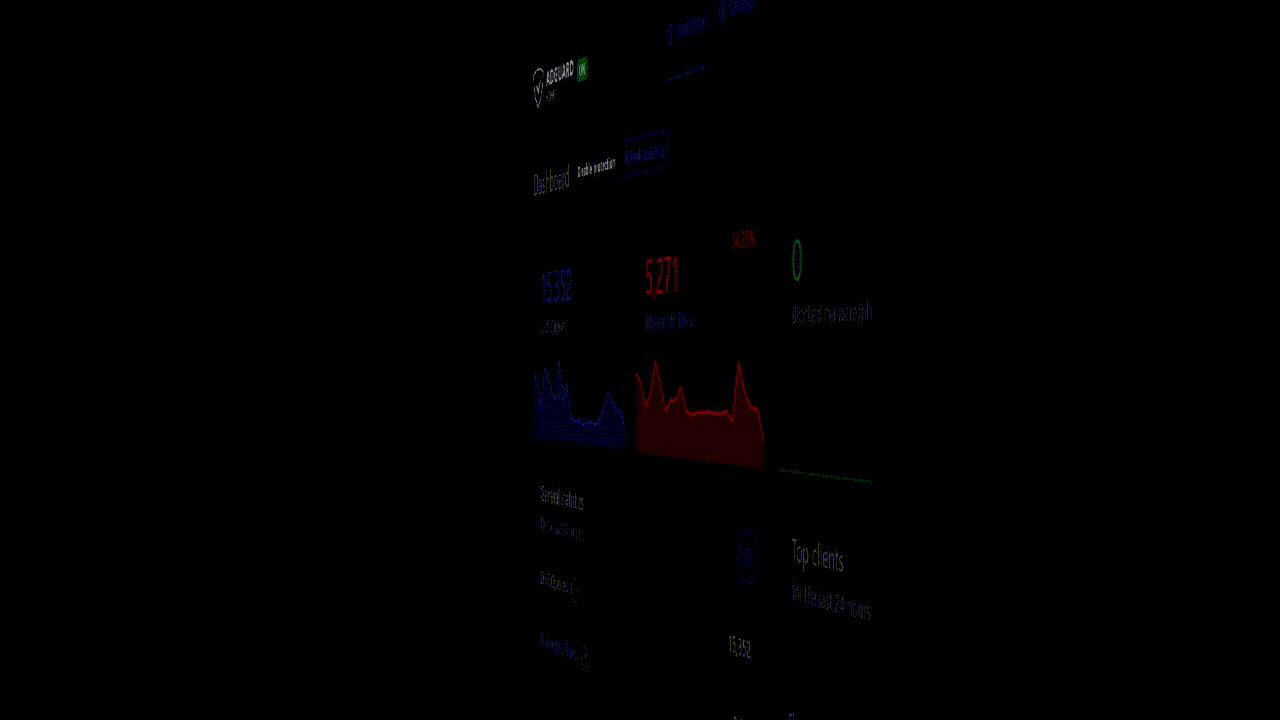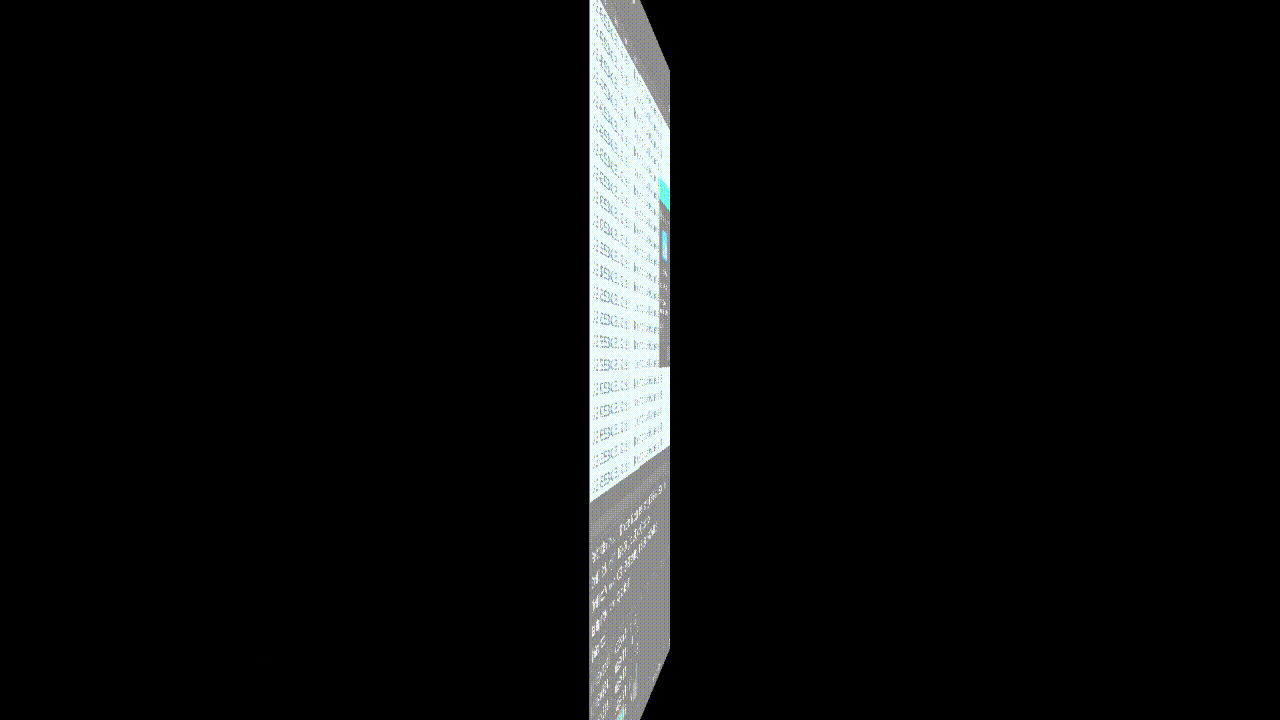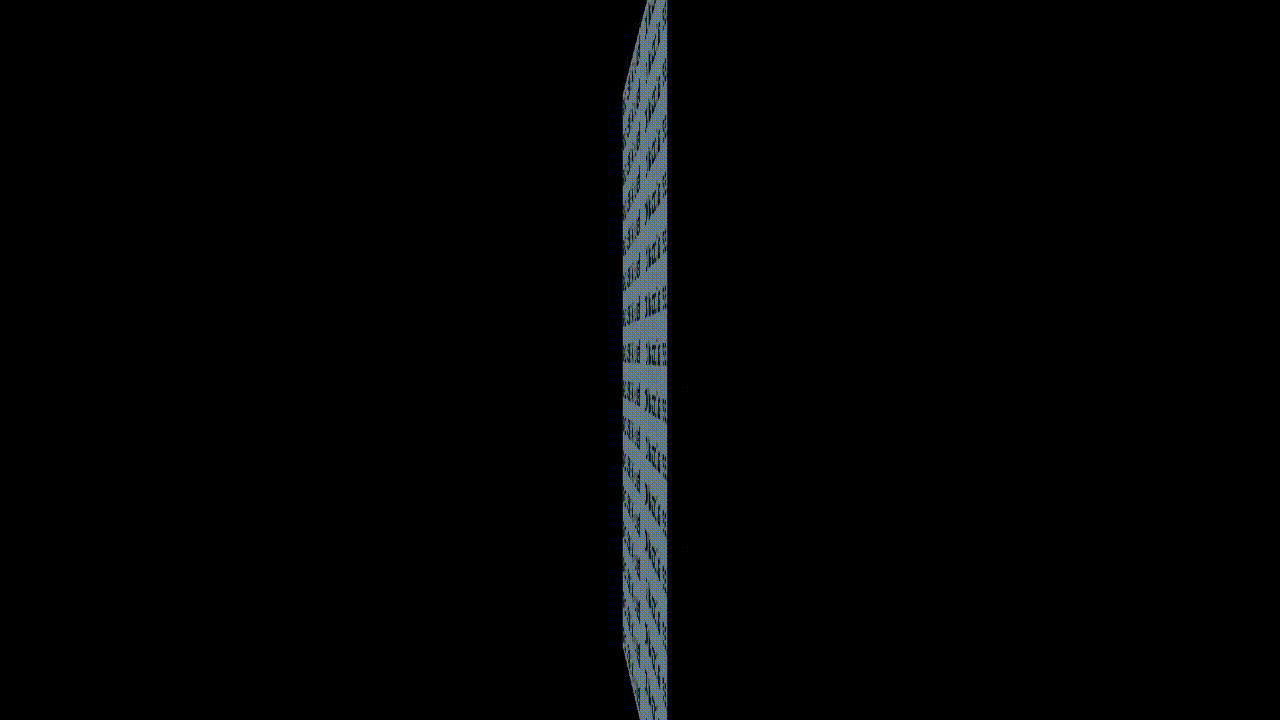



Softwares
_
AdGuard Home or
Pi-hole_Block banners, pop-ups and video advertisements network-wide
_
WireGuard or
OpenVPN_A VPN server accessible from public networks (IPv4 & IPv6)
_
Unbound or
Knot_A validating, recursive, caching DNS resolvers (DoT)
_
Stubby_DNS queries are sent to resolvers over an encrypted TLS connection providing increased privacy
_
Cloudflared Tunnel_A tunneling daemon that proxies traffic from a DNS network to your origins(DoH)
_
DNScrypt_Modern encrypted DNS protocols such as DNSCrypt v2, DNS-over-HTTPS, Anonymized DNSCrypt and oDoH (Oblivious DoH)
#
All software are free, open-source and self-hosted ABOUT | FAQ | WIKI | DISCUSS
DNS query time
Query speed results(Ethernet LAN) using
BIND9 dig tool:
- AdGuard default DNS resolvers - `60-70 msec`
- Public Cloudflare/Quad9/Google DNS Resolvers - `50-70 msec`
- Self-hosted setup - `5-10 msec`
> [!NOTE]
> Originally `0 msec` or same as ISP DNS speed but multiple blocklist with _excessive_ URLs slow down low-end devices affecting DNS query. This result was from a 1GB | 1.4GH ARM architecture. Blocklists used
🔗click here🔗.
Preview
AdGuard default vs Self-hosted:
https://user-images.githubusercontent.com/18756975/150230438-b767e86f-4e18-4791-b5fe-0813615a37a3.mp4
Public Cloudflare/Quad9/Google:
(same results if addresses are added manually in the system's network DNS option fields)
https://user-images.githubusercontent.com/18756975/150319049-3d8acdc9-624f-4b60-8ee2-b80227522252.mp4
#
# Table of contents
- [Requirements](#requirements)
- [Install Raspberry Pi OS](#install-raspberry-pi-os-)

- [Access Pi OS with SSH](#access-pi-os-with-ssh)
- [Install AdGuard Home](#install-adguard-home-)

- [Setup devices to work with Adguard](#setup-devices-to-work-with-adguard)
- [Updating Adguard](#updating-adguard)
- [Setting up AdGuard blocklist](#setting-up-adguard-blocklist)
- [Add/Remove multiple URLs](#addremove-multiple-urls)
- [Uninstall AdGuard](#uninstall-adguard)
- [Install SSL certificate](#install-ssl-certificate)


- [Install Pi-hole](#install-pi-hole-as-an-alternativeclick-here)

- [Install Unbound](#install-unbound-)

- [Install Knot](#install-knot-resolver-as-an-alternativeclick-here)

- [Setup DNS security](#setup-dns-security-)
- [Configure DoH/oDoH](#configure-dohodoh)
- [Cloudflared tunnel](#cloudflared-tunnelclick-here)

- [DNScrypt proxy](#dnscrypt-proxyclick-here)

- [Configure DoT on Unbound](#configure-dot-on-unbound)
- [Configure Stubby and Unbound](#configure-stubby-and-unbound)

- [Configure AdGuard with (DoH/DoT/oDoH)](#configure-adguard-with-dohdotodoh)
- [Monitor query logs](#use-tail-command-to-monitor-logs-in-realtime)
- [Install WireGuard](#install-wireguard-)

- [Connecting VPN to Android/iOS Phone](#connecting-vpn-to-androidios-phone)
- [Connecting VPN to Windows](#connecting-vpn-to-windows)
- [Configure WireGuard with adblocking & DNS security](#configure-wireguard-with-adblocking--dns-security)
- [Install OpenVPN](#install-openvpn-as-an-alternativeclick-here)

- [Limit traffic](#limit-traffic)
- [Disable all IPv6](#disable-all-ipv6)
- [Test Vpn](#test-vpn)

- [Extras](#extras)
- [Repository Resources](#repository-resources)
#
# Requirements
This tutorial is installed on a Raspberry Pi with Debian OS. Other Linux
operating system(𝟹𝟸/𝟼𝟺bit),
hardware or
VPS service can be used._(Raspberry Pi OS is most simple and recommended for Pi. For more experience users,
DietPi OS is also recommended)_
- A Raspberry Pi 3 or 4 version
- A router that supports port forwarding(most can)
- MicroSD USB card reader
- MicroSD card (8GB or bigger, at least Class 4)
- Ethernet cable
- (Optional if using monitor) MicroHDMI-(RPi 4) or HDMI-(RPi 3)
#
Install Raspberry Pi OS
Raspberry Pi OS comes in desktop and lite versions(use lite for
headless mode). It can be accessed with a monitor/keyboard/mouse or connect via
ssh from a terminal.
Raspberry Pi OS
cannot be setup through the
wizard anymore, the
Imager utility is needed to preconfigure an image user account.
* Install Raspberry Pi Imager: https://www.raspberrypi.com/software/
- Open Pi Imager tool and choose OS, go to advanced settings and configure user details. Then choose storage and write.

Place SD card into the Raspberry Pi, plug in Ethernet cable and boot up
## Access Pi OS with SSH
* Wait for a minute for Pi's first boot up
* Open browser and login router's admin panel(default
IP gateway address)
* Find list of all devices connected to network and copy the IP address of the Raspberry Pi. It will most likely have the hostname `raspberrypi`
* Open terminal on host machine
(Windows PowerShell or RaspController for Android&iOS).
Type the following command:
```
ssh pi@pi's IP address
```
Use right mouse button to paste text in Windows PowerShell.
Type “yes” for fingerprint question, and enter password.

Run in terminal:
```bash
sudo apt update -y && sudo apt upgrade -y
```
*_Reboot when finished_*
```bash
sudo reboot
```
**[

Return to contents

](#table-of-contents)**
#
Install AdGuard Home
Installation scripts are from
AdGuard Home main project. Follow to keep updated.
Run one of the following command in terminal:
Stable:
```bash
curl -s -S -L https://raw.githubusercontent.com/AdguardTeam/AdGuardHome/master/scripts/install.sh | sh -s -- -v
```
Beta - testing version of AdGuard Home. More or less stable versions:
```bash
curl -s -S -L https://raw.githubusercontent.com/AdguardTeam/AdGuardHome/master/scripts/install.sh | sh -s -- -c beta
```
Edge - newest version of AdGuard Home. New updates are pushed to this channel daily and might not be stable:
```bash
curl -s -S -L https://raw.githubusercontent.com/AdguardTeam/AdGuardHome/master/scripts/install.sh | sh -s -- -c edge
```
* When installation is finished, it will show the `links` to your AdGuard home page(Get Started) in terminal
* Choose `Eth0` in **Listen Interfaces** option

* Set up username&password and then login admin panel
> [!TIP]
> In general settings, can set "Query logs retention" to `24 hours`. (on forums some users state logs fill up which slows down Pi and needing a reboot, if using powerful device, no need to change settings)
## Setup devices to work with AdGuard
- For Android/Apple, go to WiFi advanced settings and select static option. In `DNS 1` field enter "Pi's IP" address

- For PC/Windows
-
IPv4
Go to network settings / change adapter options, right click in properties and select "Internet Protocol Version 4(TCP/IPv4)". Enter Pi's IP address in `Preferred DNS` server.
-
IPv6 (needed for `DoH`/`DoT`/`oDoH` to detect if using it)
Go to "Internet Protocol Version 6(TCP/IPv6)" Enter
`::1`

## Updating AdGuard
AdGuard Home can be updated from its user interface or
manually from command line.
_Use script constructed with manual commands and can be set to autorun
🔗click here🔗_.
## Setting up AdGuard blocklist
In AdGuard homepage under filters, select DNS blocklist section for adding URLs.


Aiming to promote security, safety, and sanity across the internet!

BIG THANKS

to
T145
Large list of Blocklists and Allowlists Sources
🔗click here🔗
> [!CAUTION]
> Some Blocklists can block important web content. To unblock, go to "Query Log" section, hover cursor over that specific query
(look for client IP & time) to show _unblock_ option. The links is automatically created in "Custom filtering rules" example: `@@||bitly.com^$important`(can add the websites manually as well).
## Add/Remove multiple URLs
Only one URL can be added at a time in DNS blocklist with AdGuard for now, but a python script can be used to add multiple URLs at once.
Create a new python file(bulkurls.py):
```bash
nano bulkurls.py
```
Then copy and paste script text
🔗click here🔗. Set `your AdGuard credentials` and save (control+x then y then enter).
> [!NOTE]
> If using **DietPi** install `sudo apt-get install python3-pip -y && pip install requests` for it is not currently installed by default.
To run : `sudo python3 bulkurls.py`
_(Reboot when finished)_
To **remove** change `add` in
second of last line to `remove` in bulkurls.py file.
Or just change it from command line in terminal:
```bash
sed -i 's/add_url/remove_url/g' bulkurls.py
# Revert
sed -i 's/remove_url/add_url/g' bulkurls.py
```
## Uninstall AdGuard
Run this
script from repo through network using
curl in terminal:
```bash
curl -s -L https://raw.githubusercontent.com/trinib/AdGuard-WireGuard-Unbound-Cloudflare/main/assets/scripts/remove_adguard.sh | sh
```
## Install SSL certificate
If using AdGuard Home on a `VPS(Virtual private server)`, get a
SSL certificate to make connection secure and data safe
🔗click here🔗. In this case your DNS resolver(AdGuard Home) resides outside your network, and your DNS requests have better protection from the third parties.
### _Install Pi-hole as an alternative
🔗click here🔗_
**[

Return to contents

](#table-of-contents)**
#
Install Unbound
> [!TIP]
> Before installing other DNS resolvers, it is a good idea to turn off
systemd-resolved DNSStubListener(
issue#27).
`OPTIONAL:` Installing via the package manager is the easiest option with automatic updates and stable versions. The downside is that it can be outdated for some distributions or not have all the compile-time options included that you want.
**Building and compiling** Unbound yourself ensures that you have the latest version and all the compile-time options you desire
🔗click here🔗.
For the version from package manager, run the following command in terminal:
```bash
sudo apt install unbound -y
```
> [!IMPORTANT]
> If using **DietPi** or other OS that do not auto insert `nameserver 127.0.0.1` in resolv.conf(to check - `sudo nano /etc/resolv.conf`) and want to query cache on
local hosts, just install resolvconf package and restart unbound-resolvconf.service which should be automatically set:
>
> sudo apt-get install resolvconf -y && sudo systemctl restart unbound-resolvconf.service
> Run `ping -c 3 google.com` to confirm localhost is reachable to internet. If not, set/add your default network's dns/gateway or whatever was the default
🔗click here🔗
Confirm 127.0.0.1 address interface is up:
```bash
## Install dig: sudo apt install dnsutils
dig google.com @127.0.0.1
```
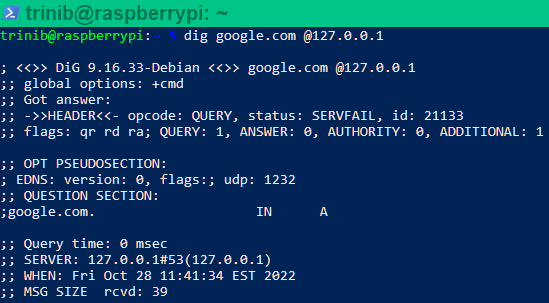
* For recursively querying a host that is not cached as an address, the resolver needs to start at the top of the server tree and query the root servers, to know where to go for the top level domain for the address being queried. Unbound comes with default built-in hints.
Download latest:
```bash
wget -O root.hints https://www.internic.net/domain/named.root && sudo mv root.hints /var/lib/unbound/
```
* This needs to update every 6 months using
cron job. Enter in command line `crontab -e`, it will ask select an editor(choose 1), paste these lines at the bottom of crontab and save (control+x then y then enter):
> 1 0 1 */6 * wget -O root.hints https://www.internic.net/domain/named.root
> 2 0 1 */6 * sudo mv root.hints /var/lib/unbound/

Skip straight ahead to configuring DoT in this [**section**](#configure-dot-on-unbound), and setup with AdGuard in this [**section**](#configure-adguard-with-dohdotodoh) if not interested in Stubby or Cloudflared or DNScrypt proxy below.
### _Install Knot Resolver as an alternative
🔗click here🔗_
**[

Return to contents

](#table-of-contents)**
#
Setup DNS Security
## Configure DoH/oDoH
Option 1 (Simple)- DNS over HTTPS only
Option 2 (Advanced) - no need for cloudflare tunnel or stubby methods- DNS over HTTPS
Oblivious DNS Over HTTPS
_Oblivious DNS Over HTTPS(oDoH) is a newly proposed open-source DNS standard built by engineers from Cloudflare, Apple, and Fastly which is supposed to increase the privacy of already existing DNS Over HTTPS_.
Anonymized-DNS
_Anonymized DNS is a lightweight alternative to Tor and SOCKS proxies, dedicated to DNS traffic. They hide the client IP address to DNS resolvers, providing anonymity in addition to confidentiality and integrity._.
## Configure DoT on Unbound
Download unbound
configuration file with DNS over TLS settings and move it to unbound folder.
Enter in terminal:
```bash
wget https://raw.githubusercontent.com/trinib/AdGuard-WireGuard-Unbound-Cloudflare/main/unbound.conf && sudo mv unbound.conf /etc/unbound/unbound.conf.d/
```
- Choose DNS provider
🔗click here🔗
Restart unbound service and check status:
```bash
sudo systemctl restart unbound && sudo systemctl status unbound
```

Run `dig google.com @127.0.0.1` and check for `NOERROR` status to confirm its connected to DNS server.
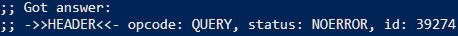
## Configure Stubby and Unbound
Use Unbound for caching and Stubby as a
TLS forwarder
> [!WARNING]
> Stubby and DNScrypt **should not** be used together when both are set to run as a forwarder in Unbound, else redundant caching will occur. Use with Cloudflare tunnel only.
`OPTIONAL:` **Building and compiling** Stubby yourself ensures that you have the latest version
🔗click here🔗.
Install the version from package manager:
```bash
sudo apt install stubby -y
```
- Download stubby
configuration file and replace with default one in stubby folder:
```bash
wget https://raw.githubusercontent.com/trinib/AdGuard-WireGuard-Unbound-Cloudflare/main/stubby.yml && sudo mv stubby.yml /etc/stubby/
```
- Forward Stubby address in Unbound upstreams. Open `sudo nano /etc/unbound/unbound.conf.d/`
`unbound.conf` and uncomment Stubby addresses(remove # infront of lines [169](https://github.com/trinib/AdGuard-WireGuard-Unbound-Cloudflare/blob/68726b2c1e24d1940ac82775be9aa76748f564d2/unbound.conf#L169)&[170](https://github.com/trinib/AdGuard-WireGuard-Unbound-Cloudflare/blob/68726b2c1e24d1940ac82775be9aa76748f564d2/unbound.conf#L170))
Or do it from command line:
```bash
awk '{sub(/[#]forward-addr: 127.0.0.1@8053/,"forward-addr: 127.0.0.1@8053") || sub(/[#]forward-addr: ::1@8053/,"forward-addr: ::1@8053")}1' /etc/unbound/unbound.conf.d/unbound.conf > unbound.conf && sudo mv unbound.conf /etc/unbound/unbound.conf.d/
```
- Choose DNS provider
🔗click here🔗
Restart stubby service and check status:
```bash
sudo systemctl restart stubby && sudo systemctl status stubby
```

## Configure AdGuard with `(DoH/DoT/oDoH)`
* In AdGuard homepage under settings, select **DNS settings**
* Delete everything from both _**Upstream**_ and _**Bootstrap DNS**_ server options and add the following for:
- DNS over TLS(unbound/knot) : `127.0.0.1:53`
- DNS over HTTPS/Oblivious DNS over HTTPS :
- `127.0.0.1:5053`(cloudflared tunnel)
- `127.0.0.1:5353`(dnscrypt proxy)
- TLS forwarder(stubby) : `127.0.0.1:8053`
- Select
Parallel Request option for DNS resolvers to work simultaneously.

- In DNS setting look for DNS cache configuration section and set cache size to `0` (caching is already handled by Unbound) and save.

Click apply and test upstreams
#### Now go to https://1.1.1.1/help in browser and these options should output 'Yes'.
> [!NOTE]
> only detects for cloudflare servers in the first 3 info lines
- [x] Connected to 1.1.1.1
- [x] DNS over HTTPS(DoH)
- [x] DNS over TLS(DoT)
- [ ] DNS over WARP

### Sometimes DoH or DoT shows no?
This could just be a fault on 1.1.1.1/help and host cause according to logs, for example DNScrypt with DNS over HTTPS shows it **does recieve a query response/PASS** although when showing "no" for DNS over HTTPS.
Query logs
https://user-images.githubusercontent.com/18756975/197397288-18c7f33b-abb3-4628-b8e3-1ad29623f693.mp4
Same goes in Unbound logs when DNS over TLS shows "no"(still gets queried):
A records(IPv4)
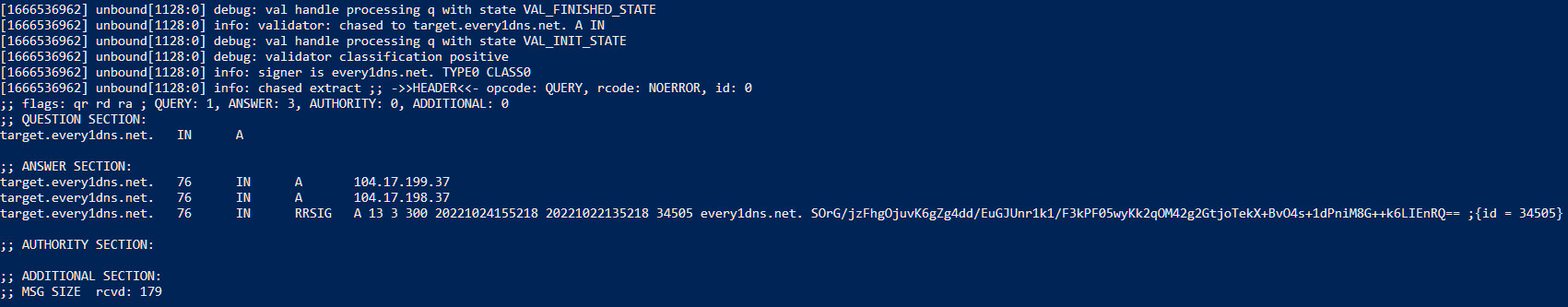
AAA records(IPv6)
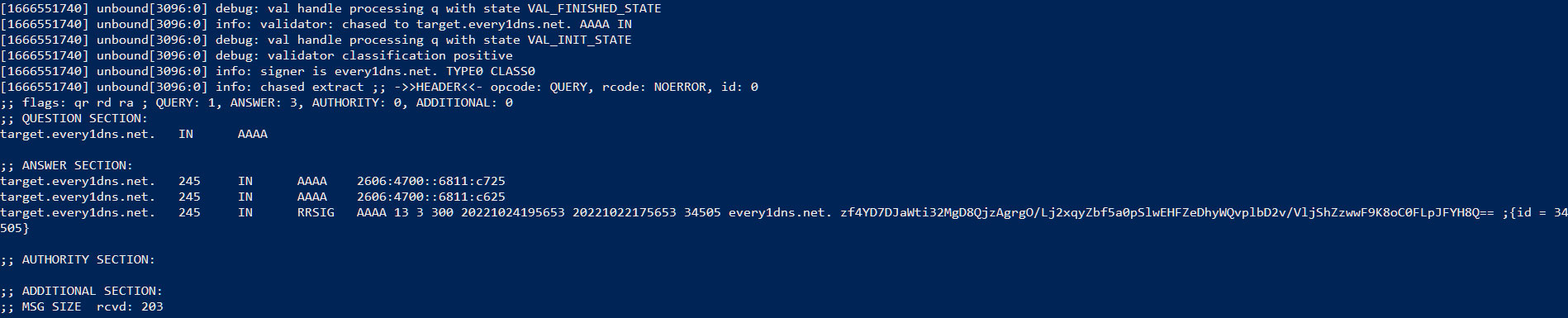
### Use
tail command to monitor logs in realtime:
```bash
## Unbound
## If using unbound from package manager, manually create log file - sudo touch /var/log/unbound.log
## and set permission - sudo chown unbound:unbound /var/log/unbound.log
## Choose verbosity level and set log path in unbound.conf - logfile: /var/log/unbound.log
## Restart unbound - sudo systemctl restart unbound
sudo tail -f /var/log/unbound.log
## DNSCrypt
sudo tail -f /var/log/dnscrypt-proxy/query.log
```
> [!TIP]
> Stable DNS resolving
🔗click here🔗
#### Other sites to test security
[browserleaks](https://browserleaks.com/dns) - should show all connected to "Cloudflare"
[dnssec](https://rootcanary.org/test.html) - should say "Yes, your DNS resolver validates DNSSEC signatures"
[dnscheck tools](https://dnscheck.tools/) - inspect your dns resolvers (DNSSEC using ECDSA P-256,DNSSEC using ECDSA P-384,DNSSEC using Ed25519)
**[

Return to contents

](#table-of-contents)**
#
Install WireGuard
> [!WARNING]
> **Before installing WireGuard**, if you do not have a external/public
static IP it will change dynamically from your internet service provider or from a router reboot. You will need to setup a dynamic DNS service with a hostname to keep automatically up-to-date with a dynamic IP
🔗click here🔗. Or else skip this.
> [!IMPORTANT]
> You also need to set up
port forwarding on your router so you can access WireGuard network anywhere like open wifi/hotspots and even from mobile data tethering.
TYPE | VALUE
------------ | -------------
Device | Raspberry Pi's hostname or IP
Protocol | UDP
Port range | 51820-51820
Outgoing port | 51820
Permit Internet access(if have) | yes
Example of my router port settings:

> [!NOTE]
> Other router brands will have a different interface look. Google search it for help. If you cannot connect from a outside network that means your ISP has blocked incoming connections and only allow outgoing, call them and ask nicely to unblock.
#

BIG THANKS

for this installation script from
Nyr. Follow to keep updated.
(
PiVPN script can also be used)
Download and run script in terminal:
```bash
wget https://git.io/wireguard -O wireguard-install.sh && sudo bash wireguard-install.sh
```
* The script is going to ask for a Public IPv4/hostname for the VPN. If you have static IP then continue or else type the dynamic DNS hostname that was created from the
instructions. For example:`trinibvpn.freeddns.org`
* For port option `press enter` for default 51820, set client name and for DNS use option 3 (`1.1.1.1`) for now.

* Wait until the installation is finished and QR code to show,
don't close. But if do, to `regenerate qrcode`, enter in terminal but replacing just the name `yourclientname.conf` file to yours:
```bash
sudo cp /root/yourclientname.conf /home/pi && sudo qrencode -t ansiutf8 < yourclientname.conf
```
> [!NOTE]
> For each device, you will need to add a new client/user
(cannot use 1 client for multiple devices at the same time). To add, re-run the script and create another user with different client name.
### Connecting VPN To Android/iOS Phone
Install the WireGuard app from Google Play or App Store:
WireGuard (Google Play): https://play.google.com/store/apps/details?id=com.wireguard.android
WireGuard (App Store): https://apps.apple.com/us/app/wireguard/id1441195209
Scan the QR code shown in the terminal with WireGuard app, select the `+ button` and use the option `Scan from QR code` to install configuration.
- Enable **kernel module backend** in settings

### Connecting VPN to Windows
WireGuard for windows: https://download.wireguard.com/windows-client/wireguard-installer.exe
* Create a `new text document` with any name on PC to copy over the text from WireGuard client configuration file.
* To see text in client config file, type in terminal:
```bash
sudo cat /root/yourclientname.conf
```
* Highlight all the text, copy and paste it in the txt file on PC and save. Then rename the extension from `txt` to `conf`. Now you have config file for that specific WireGuard client/user.
* Import the config file to WireGuard (import from file option), save and connect.
## Configure WireGuard with adblocking & DNS security
> [!NOTE]
> I think it might not make much of a difference to use DoT/DoH/oDoH with WireGuard security protocols. Though from my experience and in forums, it does not seem to cause any issues using them together. Mainly this is to achieve adblocking with a VPN on public networks.
* In WireGuard app, select your tunnel name and select edit (pencil on top right)
* Under DNS servers enter `Pi's IP`(IPv4 & IPv6) and save

### _Install OpenVPN as an alternative
🔗click here🔗_
#
### Limit traffic
Self-hosted VPNs will lose a fair percentage of internet speed from the process of tunneling through Linux system, to router, to devices. You need send traffic through your local network only for better speeds
🔗click here🔗.
#
### Disable all IPv6
#### Disable IPv6 if you don't have it or don't want it
🔗click here🔗. In result if you have weak internet, disabling IPv6 can speed up dns records and request but have less security.
#
## Test VPN
How to know if WireGuard VPN is really working?
For **windows** download Wireshark: https://www.wireshark.org/#download
Once downloaded, use the application to inspect data packets where the protocol is set to the one used by WireGuard VPN. When a packet traffic is `encrypted`, it can be read like this for example:

For **android** use PCAPdroid: https://play.google.com/store/apps/details?id=com.emanuelef.remote_capture&hl=en&gl=US
You should see all connections `closed` and status showing all `DNS port 53` and not any TLS port 443 connections from all apps. (open and use apps for PCAPdroid to scan)
**[

Return to contents

](#table-of-contents)**
***
✨ 𝘈𝘕𝘠 𝘐𝘚𝘚𝘜𝘌𝘚, 𝘍𝘐𝘟𝘌𝘚 𝘖𝘙 𝘛𝘐𝘗𝘚 𝘛𝘖 𝘔𝘈𝘒𝘌 𝘛𝘏𝘌𝘚𝘌 𝘗𝘙𝘖𝘑𝘌𝘊𝘛𝘚 𝘉𝘌𝘛𝘛𝘌𝘙 𝘗𝘓𝘌𝘈𝘚𝘌 𝘊𝘖𝘕𝘛𝘙𝘐𝘉𝘜𝘛𝘌 ✨




#
## Extras
NextDNS Client
Network CLI Tools
Secure Raspberry Pi
Auto Update Raspberry Pi
AdGuard Home Dark Theme
Improve SD Card’s lifespan
Linux Bash commands
#
## Repository Resources
https://github.com/AdguardTeam/AdGuardHome/wiki
https://docs.pi-hole.net/
https://developers.cloudflare.com/
https://unbound.docs.nlnetlabs.nl/en/latest/
https://knot-resolver.readthedocs.io/en/stable/#
https://dnsprivacy.org/dns_privacy_clients/
https://github.com/DNSCrypt/dnscrypt-proxy/wiki
https://github.com/Nyr/wireguard-install
https://github.com/T145/black-mirror






 - [Configure DoT on Unbound](#configure-dot-on-unbound)
- [Configure Stubby and Unbound](#configure-stubby-and-unbound)
- [Configure DoT on Unbound](#configure-dot-on-unbound)
- [Configure Stubby and Unbound](#configure-stubby-and-unbound)  - [Limit traffic](#limit-traffic)
- [Disable all IPv6](#disable-all-ipv6)
- [Test Vpn](#test-vpn)
- [Limit traffic](#limit-traffic)
- [Disable all IPv6](#disable-all-ipv6)
- [Test Vpn](#test-vpn)  - [Extras](#extras)
- [Repository Resources](#repository-resources)
#
# Requirements
This tutorial is installed on a Raspberry Pi with Debian OS. Other Linux operating system(𝟹𝟸/𝟼𝟺bit), hardware or VPS service can be used._(Raspberry Pi OS is most simple and recommended for Pi. For more experience users, DietPi OS is also recommended)_
- A Raspberry Pi 3 or 4 version
- A router that supports port forwarding(most can)
- MicroSD USB card reader
- MicroSD card (8GB or bigger, at least Class 4)
- Ethernet cable
- (Optional if using monitor) MicroHDMI-(RPi 4) or HDMI-(RPi 3)
#
- [Extras](#extras)
- [Repository Resources](#repository-resources)
#
# Requirements
This tutorial is installed on a Raspberry Pi with Debian OS. Other Linux operating system(𝟹𝟸/𝟼𝟺bit), hardware or VPS service can be used._(Raspberry Pi OS is most simple and recommended for Pi. For more experience users, DietPi OS is also recommended)_
- A Raspberry Pi 3 or 4 version
- A router that supports port forwarding(most can)
- MicroSD USB card reader
- MicroSD card (8GB or bigger, at least Class 4)
- Ethernet cable
- (Optional if using monitor) MicroHDMI-(RPi 4) or HDMI-(RPi 3)
#
























