ESP8266 WiFi Captive Portal
Disclaimer
This project is for testing and educational purposes. Use it only against your own networks and devices. I don't take any responsibility for what you do with this program.
About this project
WiFi captive portal for the NodeMCU (ESP8266 Module) with DNS spoofing.
The built-in LED will blink 5 times when a password is posted.
Warning! Your saved passwords will not disappear when you restart/power off the ESP8266.
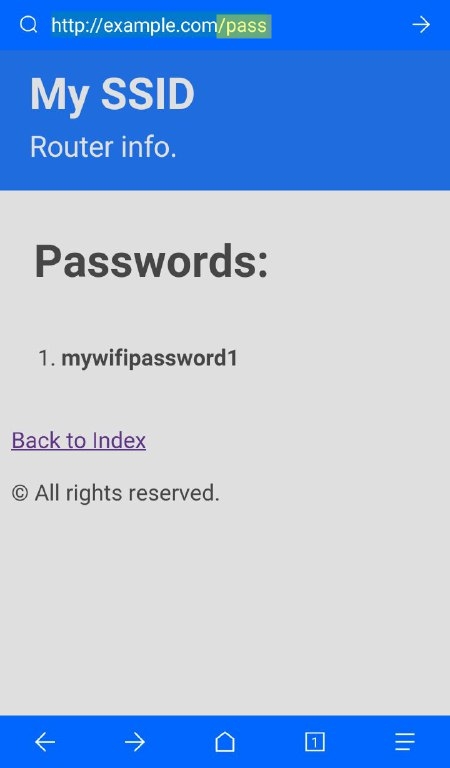
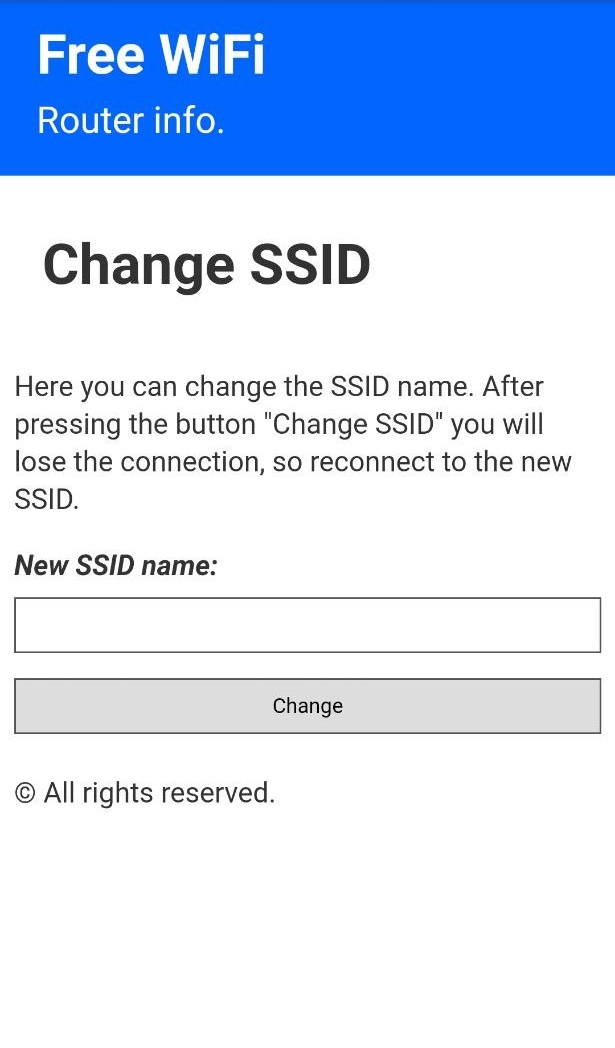
Note: If you want to see the stored passwords go to "172.0.0.1/pass". For changing the SSID, go to "172.0.0.1/ssid"
V. 2.0 (Fake sign in): https://github.com/125K/ESP8266_WiFi_Captive_Portal_2.0
Showcase
Screenshots
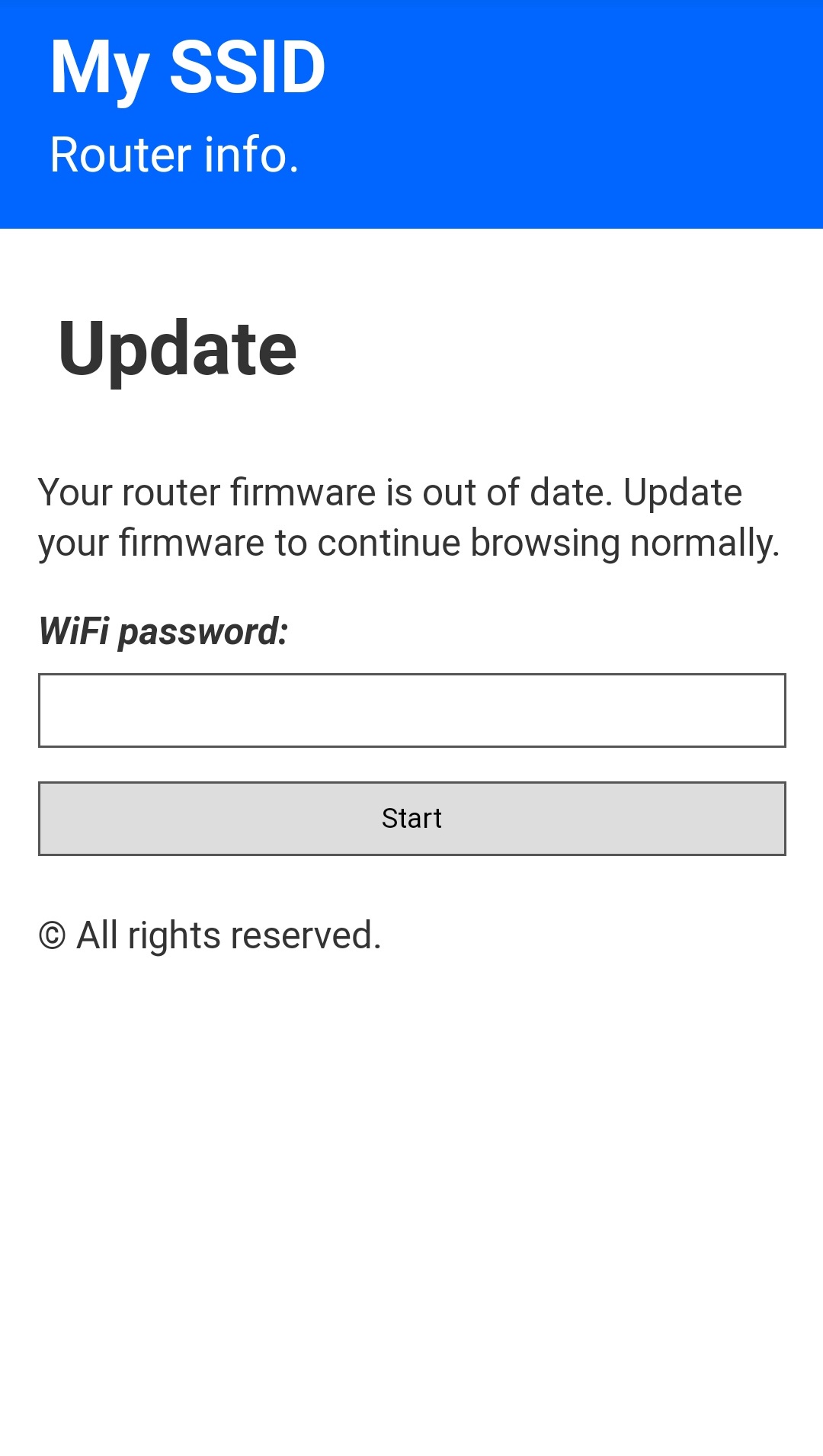
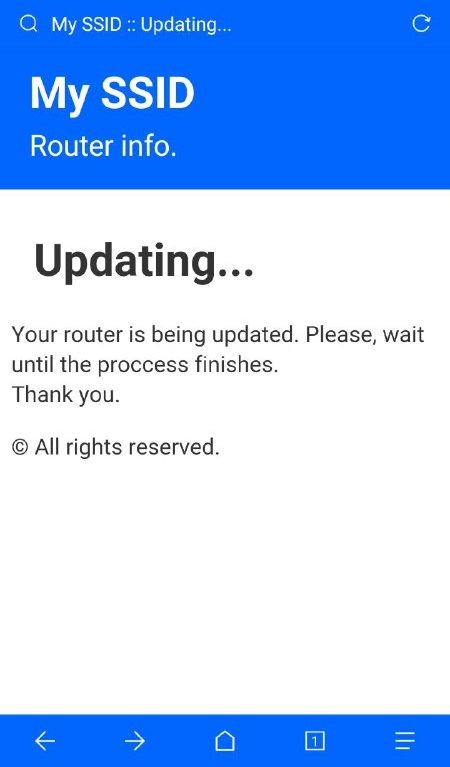
| 172.0.0.1/index | 172.0.0.1/post | 172.0.0.1/pass | 172.0.0.1/ssid |
|---|---|---|---|
| This is the main page. Here the user will write his password and send it. | This is the post page. The user will be redirected here after posting the password. | This is where the attacker can retrieve all the passwords that has been posted. | Here the attacker can change the SSID name of the Access Point on the go. |
 |
 |
 |
 |
Here you can donate if you liked my project and you want to support me:
Installation (ESP8266 Flasher - Easy way)
-
Download ESP8266 Flasher.
-
Download the release.bin file.
-
Open the ESP8266 Flasher and select the Node MCU port
- Then, go to the config tab and select the .bin file you've just downloaded.
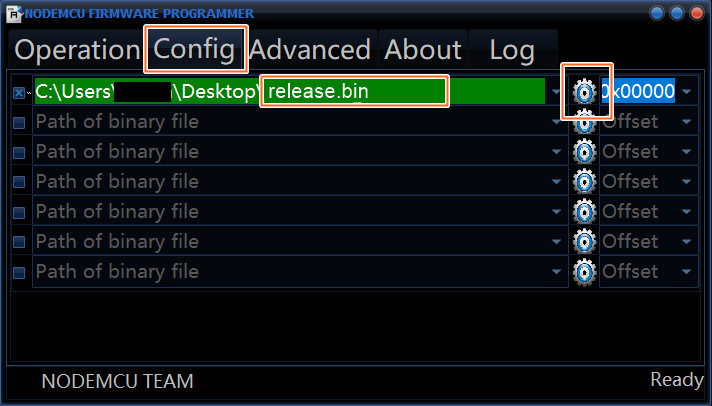
-
Finally, go back to the first tab and press "Flash"
-
Your Node MCU is ready!
Installation (Arduino IDE)
- Open your Arduino IDE and go to "File -> Preferences -> Boards Manager URLs" and paste the following link:
http://arduino.esp8266.com/stable/package_esp8266com_index.json - Go to "Tools -> Board -> Boards Manager", search "esp8266" and install esp8266
- Go to "Tools -> Board" and select you board"
- Download and open the sketch "WiFi_Captive_Portal.ino"
- You can optionally change some parameters like the SSID name and texts of the page like title, subtitle, text body...
- Upload the code into your board.
- You are done!
Check out my other projects
- WiFi-Spam: :email::satellite: Spam thousands of WiFi access points with custom SSIDs.
- PwrDeauther: :zap: Deauth a specific WiFi access point or an entire channel.