
Bluetooth-LE Security: Method, Tools and Stack
✨ News! ✨
 2020.10.13: A heap-based type confusion affecting Linux kernel 4.8 and higher was discovered in
2020.10.13: A heap-based type confusion affecting Linux kernel 4.8 and higher was discovered in net/bluetooth/l2cap_core.c.by Google Security Research ! 2020.03.26: A memory corruption issue was addressed with improved input validation by Qihoo 360 Alpha Lab !
2020.03.26: A memory corruption issue was addressed with improved input validation by Qihoo 360 Alpha Lab !
BLE Vulnerability TOP5

Table of Content
📂 BLE-Security-Attack&Defence
|-- 📂 BLE Vulnerability TOP5
| |-- 📂 BlueBorne
| |-- 📂 BleedingBit
| |-- 📂 SweynTooth
| |-- 📂 BtleJuice
| |-- 📂 BLE-CTF
|-- 📂 ble-stack
| |-- 📂 Mynewt-Nimble
| |-- 📂 nRF5_SDK_15.0.0_a53641a
| |-- 📂 PyBluez
| |-- 📂 LightBlue
|-- 📂 cap - capture package
| |-- 📂 CrackLE
| |-- 📂 TI-BLTE2Pcap
| |-- 📂 blefuzz_V21
| |-- 📂 Fuzzing Bluetooth
|-- 📂 image
|-- 📂 tools - hardware&sofrware
| |-- 📂 Ubertooth
| |-- 📂 GATTacker
| |-- 📂 BladeRF
| |-- 📂 HackRF
| |-- 📂 Adafruit-BluefruitLE
...Bluetooth LE Vulnerabilities
| 1. |  |
BlueBorne: A New Class of Airborne Attacks that can Remotely Compromise Any Linux/IoT Device
In this talk we will present the ramifications of airborne attacks, which bypass all current security measures and provide hackers with a contagious attack, capable of jumping over "air-gapped" networks...
|
| 2. |
|
BtleJuice: the Bluetooth Smart Man In The Middle Framework
A lot of Bluetooth Low Energy capable devices are spread since the last few years, offering a brand new way to compromise many “smart” objects: fitness wristbands, smart locks and padlocks and even healthcare devices. But this protocol poses some new challenges...
|
| 3. |  |
You had better secure your BLE devices
Sniffing and attacking Bluetooth Low Energy devices has always been a real pain. Proprietary tools do the job but cannot be tuned to fit our offensive needs, while opensource tools work sometimes, ...
|
| 4. |  |
BLEEDINGBIT - Takeover of Aruba Access Point Access Point 325
In this demo, Armis will demonstrate the takeover of an Aruba Access Point Access Point 325 using a TI cc2540 BLE chip. For more information, please visit https://armis.com/bleedingbit.
|
| 5. | 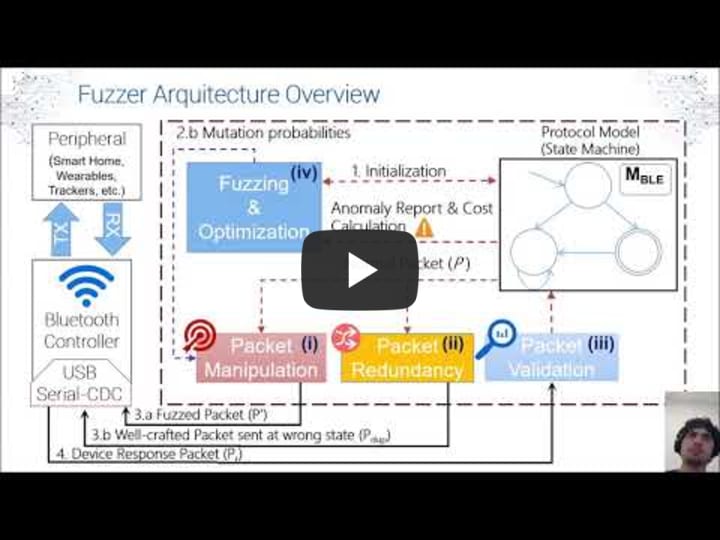 |
SweynTooth: Unleashing Mayhem over Bluetooth Low Energy
The Bluetooth Low Energy (BLE) is a promising short-range communication technology for Internet-of-Things (IoT) with reduced energy consumption. Vendors implement BLE protocols in their manufactured devices compliant to Bluetooth Core Specification. Recently, several vulnerabilities were discovered in the BLE protocol ...
|
| 6. |  |
BLESA: Spoofing Attacks against Reconnections in Bluetooth Low Energy
In this paper, we analyze the security of the BLE link-layer, focusing on the scenario in which two previously-connected devices reconnect. Based on a formal analysis of the reconnection procedure defined by the BLE specification, we highlight two critical security weaknesses in the specification. As a result, even a device implementing the BLE protocol correctly may be vulnerable to spoofing attacks...
|
| 7. | 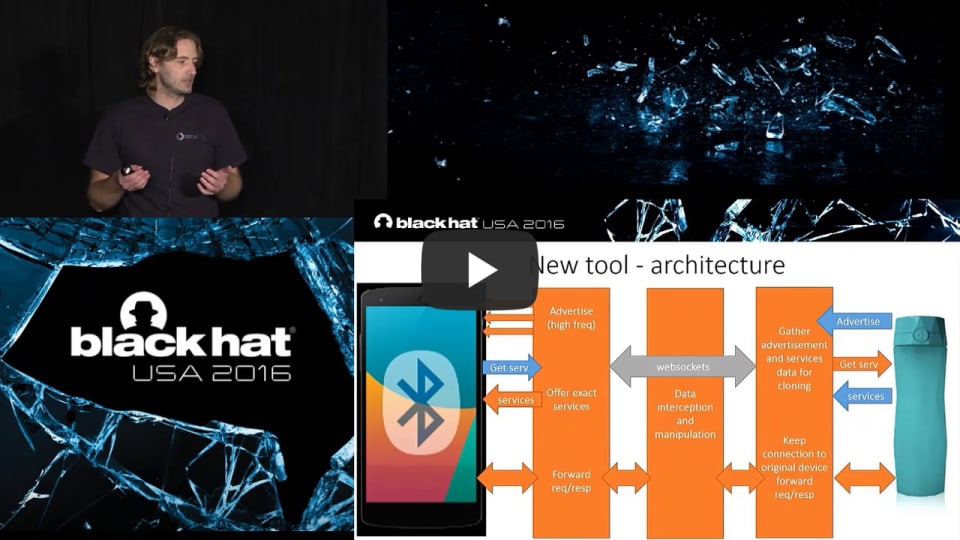 |
Gattacking Bluetooth Smart Devices - Introducing a New BLE Proxy Tool
Using a few simple tricks, we can assure the victim will connect to our impersonator device instead of the original one, and then just proxy the traffic - without consent of the mobile app or device. And here it finally becomes interesting - just imagine how many attacks you might be able to perform with the possibility to actively intercept the BLE communication....
|
| 8. |  |
BIAS: Bluetooth Impersonation AttackS
The Bluetooth standard provides authentication mechanisms based on a long term pairing key, which are designed to protect against impersonation attacks. The BIAS attacks from our new paper demonstrate that those mechanisms are broken, and that an attacker can exploit them to impersonate any Bluetooth master or slave device. Our attacks are standard-compliant, and can be combined with other attacks, including the KNOB attack. In the paper, we also describe a low cost implementation of the attacks and our evaluation results on 30 unique Bluetooth devices using 28 unique Bluetooth chips. 📑 IEEE Symposium on Security and Privacy
|
| 9. |  |
BLEKey: Breaking Access Controls With BLEKey
RFID access controls are broken. In this talk, we will demonstrate how to break into buildings using open-source hardware we are releasing.Over the years, we have seen research pointing to deficiencies in every aspect of access control systems: the cards...
|
| 10. |  |
MASHaBLE: Mobile Applications of Secret Handshakes Over Bluetooth LE
In this talk, we present new applications for cryptographic secret handshakes between mobile devices on top of Bluetooth Low-Energy (LE). Secret handshakes enable mutual authentication between parties that did not meet before (and therefore don't trust each other) but are both associated with a virtual secret group or community...
|
| 11. |  |
Safe Mode Wireless Village - The Basics Of Breaking BLE v3
Evolving over the past twenty-two years, Bluetooth, especially Bluetooth Low Energy (BLE), has become the ubiquitous backbone ...
|
| 12. |  |
Key Negotiation Of Bluetooth (KNOB): Breaking Bluetooth Security
We present an attack on the encryption key negotiation protocol of Bluetooth BR/EDR. The attack allows a third party, without knowledge of any secret material (such as link and encryption keys), to make two (or more) victims agree on an encryption key with only 1 byte (8 bits) of entropy. Such low entropy enables the attacker to easily brute force the negotiated encryption keys, decrypt the eavesdropped ciphertext, and inject valid encrypted messages (in real-time)....
|
| 13. |  |
Bluetooth Reverse Engineering: Tools and Techniques
With the continuing growth of IoT, more and more devices are entering the market with Bluetooth. This talk will shed some light on how these devices use Bluetooth and will cover reverse engineering techniques that in many cases can be accomplished with hardware you already have! Whether you're a Bluetooth newbie or a seasoned pro, you’ll learn something from this talk....
|
| 14. |  |
Apple bleee: What happens on your iPhone, stays on your iPhone
Handoff All Your Privacy – A Review of Apple’s Bluetooth Low Energy Continuity Protocol ....
|
Legend:
| Type | Icon |
|---|---|
| Research | |
| Slides | |
| Video | |
| Website / Blog post | |
| Code | |
| Other |
▲ Adversarial examples
▲ To-Do
- 2020.10 BleedingTooth CVE-2020-12351 CVE-2020-12352 CVE-2020-24490
- 2020.04 BIAS CVE-2020-10135
- 2020.03 Bluewave CVE-2020-3848 CVE-2020-3849 CVE-2020-3850
- 2020.03 BLURtooth CVE-2020-15802
- 2020.03 BLESA CVE-2020-9770
- 2020.03 KNOB CVE-2019-9506
Code of Conduct
Citation
Use this bibtex to cite this repository:
@misc{BLE Security,
title={Bluetooth LE-Security: Method, Tools and Stack},
author={Charmve},
year={2020.09},
publisher={Github},
journal={GitHub repository},
howpublished={\url{https://github.com/Charmve/BLE-Security-Attack-Defence}},
}*updade on 2021/08/05 @ Charmve


